Security Anti-Patterns: Mistakes to Avoid (re:Invent 2017)
- Account Structure Anti-Patterns
- Network Design Anti-Patterns
- InfoSec Auditing
- Example: Amazon RDS At-Rest Encryption Audit
- Software Delivery Anti-Patterns
- CFN-NAG
Anti-Pattern: A common response to a recurring problem that is usually ineffective and risks being high counterproductive.
Risks associated with Security Anti-Patterns
- Lack of SecOps agility
- Slow threat assessments
- Can’t patch fast enough
- Reactive security posture
- Lack of business agility
- Slow to onboard new customers
- Hard to practice true DevOps
- Rogue dev projects
Types of Security Anti-Patterns
- Account Structure
- Network Design
- InfoSec Auditing
- Software Delivery
Account Structure Anti-Patterns
- MFA tied to person’s mobile phone
- Root login: one person’s inbox
- If someone leaves the company, this could put the company in trouble
- No one should log into the account root! Use IAM only!
- Anti-Pattern: AWS Account Overcrowding
- Hard to manage permissions
- Ambiguous responsibility boundaries
- Blast radius
Network Design Anti-Patterns
- Trusted IP Access w/o Client Auth
- Routing is not security
- Doesn’t identity end users
- Not defense in depth
- Not highly scalable
- Best Practice: Implement Authentication and Authorization
- Network Egress Backhauling
- Some companies send traffic to the data center for traffic inspection proxy
- Requires AWS Direct Connect
- Can be solved with having restricted egress via exit VPC
- Exit VPC: Pool of EC2 instances running host based filtering controls
- Can consider other AWS partners providing third-party solutions
InfoSec Auditing
- Anti-Pattern: Security Questionnaires
- Point-in-time: not continuous
- Not based on standards
- No independent verification
- Not highly scalable
- Best Practice: Attestations Instead of Questionnaires
- SOC 2, PCI DSS, HIPAA, etc…
- Standardized Controls
- Third-party SQAs verify compliance
- Recertification cadence
- Best Practice: Align with the Standard Controls
- Higher priority for overlapping controls among different compliances
- Anti-Pattern: Manual Technical Auditing
- Manual technical audits
- Not highly scalable
- Inconsistent process
- Typically reactive
- Best Practice: Continuous Automated Auditing
- DevSecOps: security as code
- Proactive controls enforced by code
- Continuous evidence-based auditing
- Continuous detective controls
- Amazon CloudWatch Logs + Alarams
- Amazon Inspectors for EC2
- Amazon Macie for Amazon S3
- Data security and data privacy service that helps you discover, monitor, and protect your sensitive data in Amazon S3.
- Discovery jobs to analyze data in S3 buckets that you specify
- AWS Trusted Advisor
- AWS Config rules
- Cloud Conformity
- Cloud Custodian
- evident.io
- Dome9
- cfn-nag
- … and many more!
- DevSecOps: security as code
- Anti-Pattern: Not Using AWS Native Managed Services
- Methodology sprawl: audit complications + patch drift
- Best Practice: Consistency and Compliance from AWS-Managed Services
- Best Practice: Train Your Technical Auditors
- AWS Auditor Learning Path
- AWS Tech Essentials
- Goal: DevSecOps
Example: Amazon RDS At-Rest Encryption Audit
import boto3
ec2 = boto3.client('ec2')
regions = ec2.describe_regions()
# Lambda invoked by a CloudWatch Scheduled Event
def handler(event, context):
# scan each aws region
for reg in regions['Regions']:
# check each RDS instance in region
rds = boto3.client('rds', region_name = reg['RegionName'])
try:
dbis = rds.describe_db_instances()['DBInstances']
for dbi in dbis:
print '{} {} {}'.format(
reg['RegionName'],
dbi['DBInstanceIdentifier'],
dbi['StorageEncrypted']
)
Software Delivery Anti-Patterns
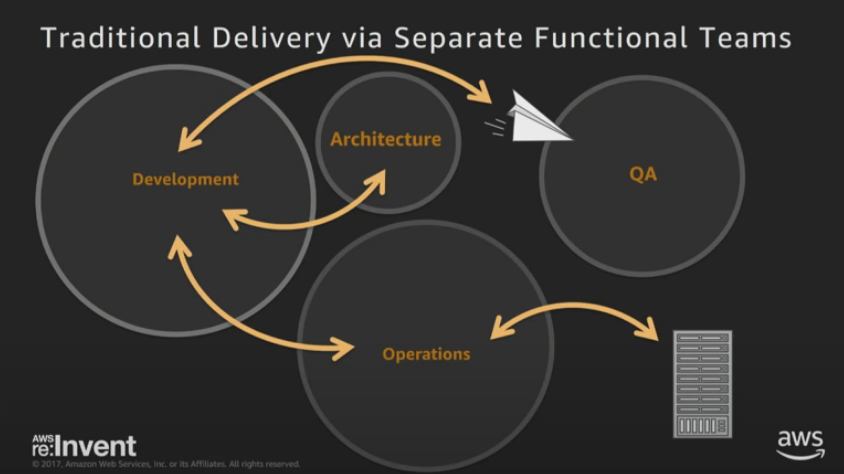
- Anti-Pattern: Over-the-Wall Software Delivery
- Dev/QA/Ops are kept in separate teams
- Manual handoff processes
- Ci/CD logistically blocked
- Tight controls and guardrails
- Post-deployment security checks
- Infrequent release cycles
- Infrequent patch rollouts Best-Practice
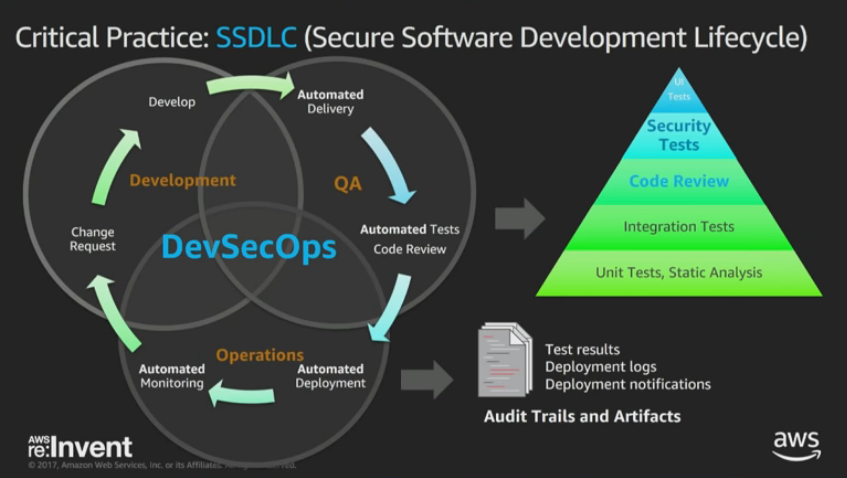
- adjust SDLC to include DevSecOps throughout the organization
- Security tests should be included in every stage
- Change review process
- DevSecOps monitoring and alerts
CFN-NAG
The cfn-nag tool looks for patterns in CloudFormation templates that may indicate insecure infrastructure. Roughly speaking, it will look for:
- IAM rules that are too permissive (wildcards)
- Security group rules that are too permissive (wildcards)
- Access logs that aren’t enabled
- Encryption that isn’t enabled
- Password literals