2 - Blockchain - The Technical Side
Public an private keys are large integer numbers and they are represented using a separate Wallet Import Format (WIF), consisting of letters and numbers.
Private key is used to generate a signature for each blockchain transaction a user sends out. It is used to confirm that the transaction has come from the user and also prevents the transaction from being altered by anyone once it has been issued.
You sign the cryptocurrencies you send to others using a private key.
Private key derives public key. With a has function public key is transformed to address visible to everyone. You can receive cryptocurrencies to your address.
Cryptographic Hash Functions
Collision when two inputs to a hash function produce the same output is extremely unlikely to happen.
Hash functions are deterministic - the same input will always yield the same output.
Bitcoin uses a SHA-256. Ethereum blockchain uses a hashing algorithm called Ethash. Hash created with Ethash looks like this:
0xb846300e188829d1b819389b31cef3b9cfaf335082ee66f830a875f1c1beb396
When data is written to the block it’s hashed. This principle allows the nodes participating in the blockchain to detect any changes to data.
Hashed data is used to create a link between each specific block. Hash of each previous block is written into the block in the chain and then hashed - producing the current block’s hash. This means that the current block hash will contain the prior hash.
Data written for the blockchain is considered permanent, making blockchain immutable.
Blockchain relies on public key cryptography to acknowledge the idea of ownership on the blockchain.
Process of miners verifying actions on the blockchain is known as a proof of work.
Message Encryption
Bob wants to send message to Alice
Bob uses Alice’s public key to encrypt the message
Alice decrypts the message using her private key
Message Signing
Bob uses his private key to create digital signature of the message
Alice uses Bob’s public key to verify the content of the message and that the message is from Bob
Merkle Tree
Every 2 nodes in this binary tree will be hashed together and merged into a single hash. As the result hash root is obtained.
Verifying that a data chunk is part of the bunch represented by a merkle root will require less computation.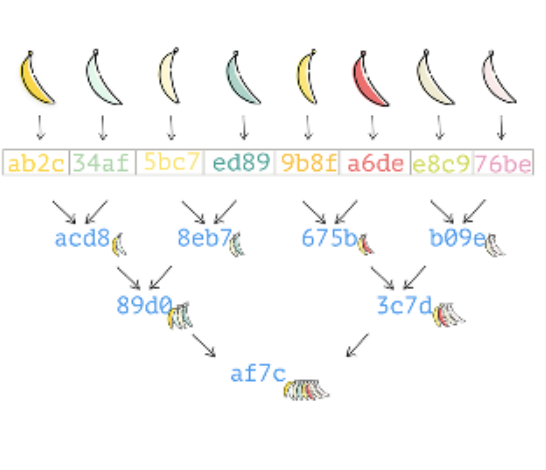
The Bitcoin blockchain uses Merkle proofs in order to store the transactions in every block.
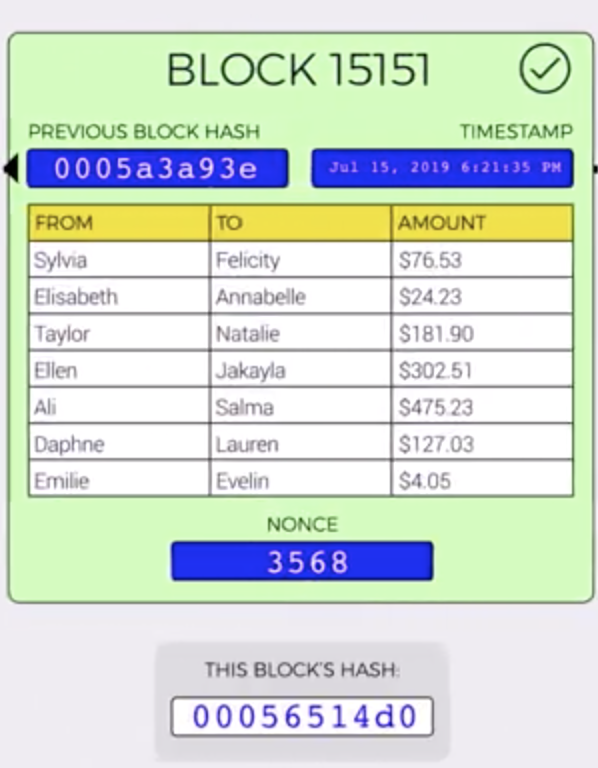
Anatomy of the Block
- Transactions (limited to 1mb in size, 1500 - 2000 transactions)
- Block height: unique, auto-incremental number, identifying block’s position
- Timetstamp
- Nonce
- Hash of each previous block is written into the block in theHash of the previous block in the chain
Validity: not all blocks are valid. Finding a valid block = mining. Blockchains have an arbitrary “difficulty” setting which changes how hard it is to find a block. The work required to create a valid block is where value comes from. Miners are rewarded financially for finding a block. This is the work in “proof of work”.
Based on the set difficulty you have to find a nonce which will result in the block hash value to be below the threshold. As a result of this the block will become valid and you will receive a reward for your work - currently it’s 12.5 bitcoins.
Tampering a single transaction will invalidate all the subsequent transactions and will require someone to recalculate the valid nonces for them.
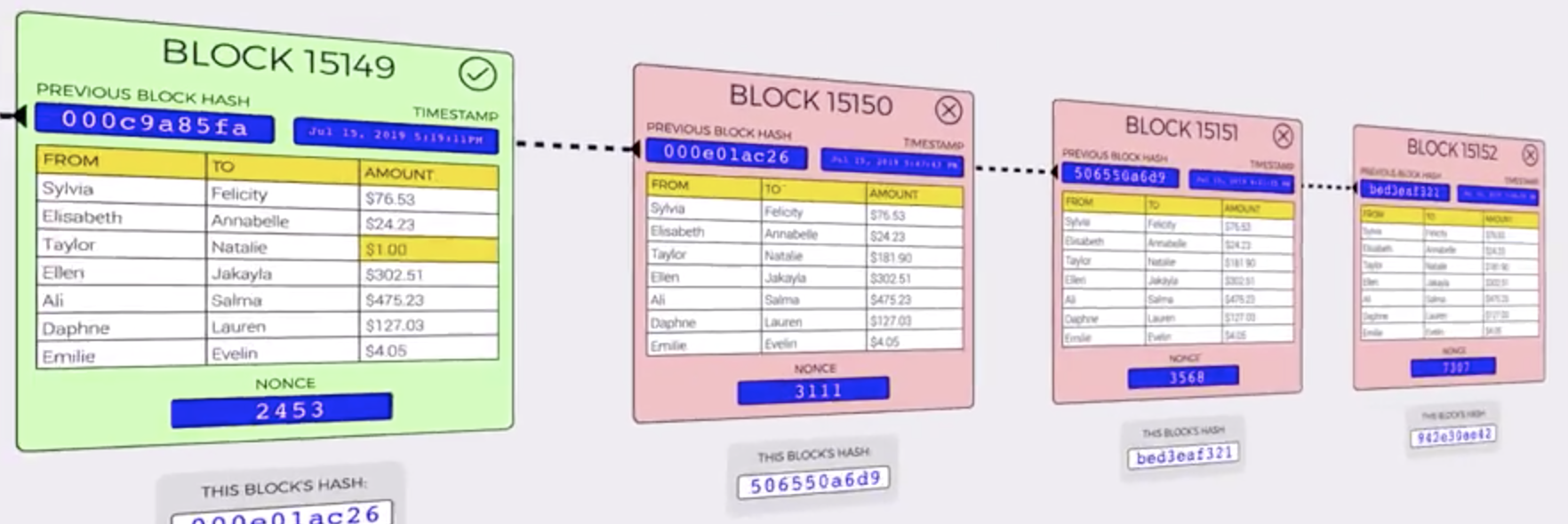
Blockchain protocols work on peer-to-peer network model. (e.g. Ethereum network, Bitcoin and Bittorent). There are 3 types of nodes operating in blockchain network: Full Node, Light Node, Miners.
