AWS Best Practices for DDoS Resiliency (2019)
Protecting the business from the impact of Distributed Denial of Service attacks (DDoS):
- Maintaining availability and responsiveness of your application
- Avoid unnecessary cost of scaling infrastructure in response to an attack
Denial of Service Attacks
DDoS attacks:
- Uses multiple sources, distributed groups of malware infected devices to orchestrate an attack against a target
- Hosts generate a flood of packets or requests to overwhelm the target
- DDoS are most common at layers 3,4,6 and 7 of the OSI model
Examples of attacks:
- HTTP floods, DNS query floods - Application layer
- TLS Abuse - Presentation layer
- Interhost communication - Session layer
- SYN floods - Transport layer
- UDP reflection attacks - Network layer
- Physical addressing - Data link layer
- Media, signal and binary transmission - Physical layer
Infrastructure Layer Attacks
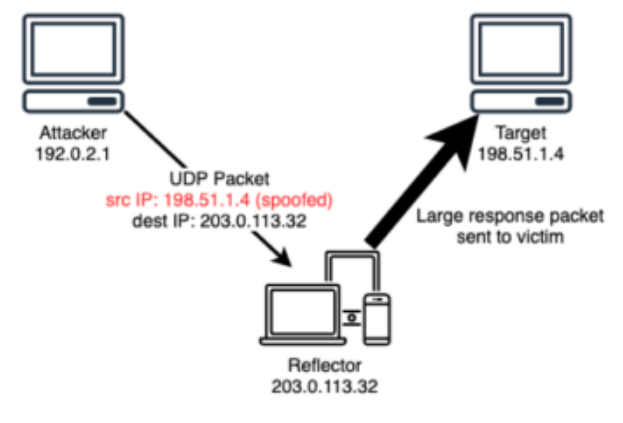
UDP Reflection Attack:
- Attacker generates a valid UDP request
- Attacker spoofs the source IP, by indicating the victim’s IP address
- Request is sent to an intermediate server
- Server is tricked into sending its UDP response packets to the victim
- Response is several times larger then request
- Amplification factor is the ration of response size to request size
SYN Flood Attacks
- Malicious client sends a large number of SYN packets, without sending the final ACK packets to complete the handshakes
- Server is waiting for a response to the half-open TCP connections
- Server runs out of capacity to accept new TCP connections
Application Layer Attacks
- HTTP flood attack
- Attacker sends HTTP requests that appear to be from a role user of the web application
- HTTP floods may target a specific resource
- HTTP floods may attempt to emulate human interaction with application, making it increasingly difficult to use techniques like request rate limiting
- Cache-busting attacks
- Query string variations are used to circumvent content delivery network (CDN) caching
- CDN must contact the origin server and that can cause additional strain on the application web server
- WordPress XML-RPC flood attack
- Known as WordPress pingback flood
- Attacker misuses the XML-RPC API function
- Pingback feature allows Site A to notify site B about link created, which will then attempt to fetch Site A to verify existence of the link
- Attacker misuses this capability to cause Site B to attack Site A
- DNS Query Flood
- Attacker uses many well-formed DNS queries to exhausted the resources of DNS server
- May include cache-busting component, randomizing the subdomain string to bypass the local DNS cache of any given resolver
- TLS attacks
- TLS is computationally expensive
- Attacker can reduce server’s availability by sending unintelligible data
- Attacker may complete the TLS handshake but perpetually renegotiates the encryption method
- Attacker can attempt to exhaust server resources by opening and closing many TLS sessions
These attacks are not DDoS attacks, but their automated nature can look similar to DDoS attack:
- Scraper Bots
- Automate attempts to access a web application to steal content or record competitive information, e.g. pricing
- Brute force and credential stuffing
- Gaining unauthorized access to secure areas of an application
Mitigation Techniques
- AWS Shield Standard Protection
- Applies to all customers with no additional charges
- Most frequently occurring network and transport layer DDoS attacks
- Use Amazon CloudFront and Amazon Route 53
- Using Edge services, operating from edge locations improves DDoS resilience of your application
- AWS Shield DDoS mitigation systems are integrated with edge services
- Stateless SYN Flood mitigation techniques verifies the incoming connections before passing them to the protected service
- Automatic traffic engineering systems that can disperse or isolate the impact of large volumetric DDoS attacks
- AWS WAF - application layer defense
- AWS Shield Advanced
- Protects an application hosted on any AWS region
- Available for Classic Load Balancer, Application Load Balancer and Elastic IP Addresses
- Protect Network Load Balancer (NLB) or EC2 instances using Shield Advanced with EIPs
- Available globally from CloudFront and Route 53
- AWS WAF
- Allows to mitigate application layer flood attacks
- Block IP addresses using rate-based rules
- Use AWS Marketplace solutions to block malicious IP addresses that are included in reputation lists
- Review web server logs and WAF’s logging to understand the traffic that is being analyzed by your Web ACL
- Whitelist only Query String parameters that are relevant to be cached for your application, to mitigate cache-busting attacks
- AWS Firewall Manager
- Allows to centrally configure and manage AWS WAF rules across your organization
- AWS Organizations Master account can designate an administrator account
- Administrator account is authorized to create Firewall Manager policies
- Also allows creating policies to manage AWS Shield resource and VPC security groups
- Attack Surface Reduction
- Limit internet exposure of internal resources (e.g. Database, worker nodes behind Load Balancers …)
- Obfuscating AWS Resources
- Use SGs and NACLs
- If using CloudFront with an origin inside VPC, AWS Lambda should be used to automatically update your SG rules to allow CloudFront traffic
- Malicious users cannot bypass Amazon CloudFront and WAF
- Use X-Shared-Secret to help validate that requests made to your origin were sent from Amazon CloudFront
- Use API Gateway as an entryway to applications running on EC2
- Help protect the internal resources
- Use x-api-key to protect against direct traffic to API Gateway (CloudFront traffic only)
- Protect your backend from excess traffic by configuring standard or burst rate limits for each method in your REST APIs
- Limit internet exposure of internal resources (e.g. Database, worker nodes behind Load Balancers …)
- ALB, Auto Scaling
- Scale to absorb application layer traffic
- CloudWatch alarms can be set to initiate Auto Scaling events
- Ensuring enough transit capacity and diversity is available
- Instances with 25 Gigabit interface, or enhanced networking can handle larger volume of traffic - this helps prevent interface congestion
- Use CloudFront and Load Balancers
- Amazon Cloud Front, Application Load Balancer, Classic Load Balancers or Network Load Balancer handle TLS negotiation
- This protects your application from TLS-based attacks
- Scales to handle TLS abuse attacks
- ALB can route only well-formed requests, mitigating common DDoS attacks like SYN floods or UDP reflection attacks
- Offload traffic by leveraging CloudFront caching at edge
- For Amazon S3 buckets, use AWS CloudFront with Origin Access Identity (OAI) to protect your bucket
AWS Shield Advanced Features:
- Access to the AWS DDoS Response Team (DRT) for assistance in mitigating DDoS attacks that impact application availability
- DDoS attack visibility by using the AWS Management Console, API and CloudWatch metrics / alarms
- Access to Global Threat Environment dashboard (overview of DDoS attacks observed and mitigated by AWS)
- Access to AWS WAF - at no additional cost - for the mitigation of application layer DDoS attacks (used with Amazon CloudFront or ALB)
- Automatic baselining of web traffic attributes, when used with AWS WAF
- Access to AWS Firewall Manager, at no additional cost, for automated policy enforcement
- Sensitive detection threshold which routes traffic into DDoS mitigate system and can improve time-to-mitigate attacks against Amazon EC2 or NLB, when used with EIP
- Cost protection allowing to request a limited refund of scaling-related costs that result from DDoS attack
- Enhanced SLA that is specific to AWS Shield Advanced customers
Monitoring
Most common CloudWatch Metrics used to detect and react to DDoS attacks:
- AWS Shield Advanced
DDoSDetectedDDoSAttackBitsPerSecondDDoSAttackPacketsPerSecondDDoSAttackRequestsPerSecond
- AWS WAF
AllowedRequestsBlockedRequestsCountedRequests
- Amazon CloudFront
RequestsTotalErrorRate
- Amazon Route 53
HealthCheckStatus
- ALB
ActiveConnectionCountConsumedLCUs-> number of load balancer capacity units used by your load balancerHTTPCode_ELB_4XX_CountHTTPCode_ELB_5XX_CountNewConnectionCountProcessedBytesRejectedConnectionCountRequestCountTargetConnectionErrorCountTargetResponseTimeUnHealthyHostCount
- NLB
ActiveFlowCount-> total number of concurrent TCP flows or connections from clients to targetsConsumedLCUs-> number of load balancer capacity units used by your load balancerNewFlowCountProcessedBytes
- Auto Scaling
GroupMaxSize
- Amazon EC2
CPUUtilizationNetworkIn-> number of bytes received by the instance on all network interfaces
Support
- Consider subscribing to Business Support with 24x7 access to Cloud Support Engineers to assist with DDoS attack issues
- Consider Enterprise SUpport for mission critical workloads for fastest response from a Senior Cloud Support Engineer
- AWS Shield Advanced gives you access to DRT - AWS DDoS Response Team