Docs > AWS WhitePapers & Deep Dives > Best Practices for Managing Security Operations on AWS (re:Invent 2017)
Best Practices for Managing Security Operations on AWS (re:Invent 2017)
- Boundaries
- Consistent Controls
- Test often, fail early
- Closed-Loop Mechanisms
- Full Stack
- Practice
- Visibility
Boundaries
- In-VPC boundaries
- SGs, NACLs
- AWS IAM Resource level constraints
- VPC as the boundary (single account)
- Equivalent to separate networks
- Peering, routing
- AWS account as the boundary
- Highest degree of segregation
- By data classification
- Business unit
- Workload
- Functional
- Highest degree of segregation
Considerations:
- How to aggregate logging, e.g. AWS account for logging
- SecOps may require a dedicated account
Consistent Controls
- Setting up CodePipeline for CloudFormation templates
- Allows static code analysis
- Allows TestDeployment in a spare environment
- Consider Automating AWS account creation if required
- Provision stacks across AWS accounts using CloudFormation StackSets
Test often, fail early
- Commit phase: source-control changes
- Static code analysis: analyze the CFN templates against a set of security rules
- Acceptance phase: dev environment
- Dynamic analysis: run template in sandbox/acceptance test environment
- Capacity/integration/staging phases: pre-prod environment
- Load, performance, penetration and failover testing
- Production phase: prod environment
- Deploy
Closed-Loop Mechanisms
- Control
- Monitor
- Fix
Spectrum of Options:
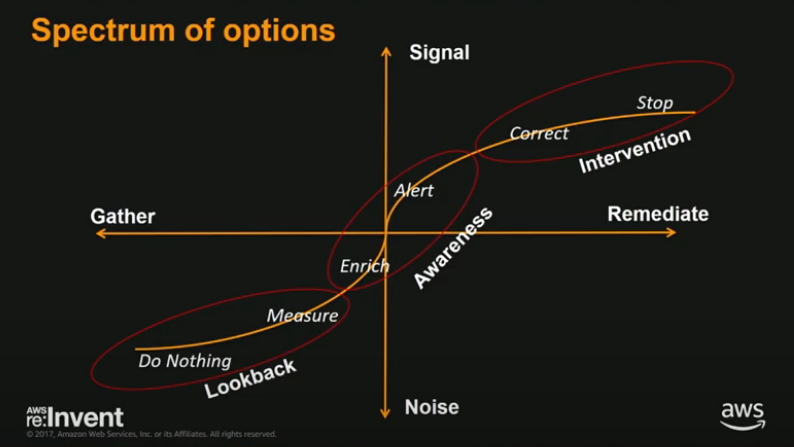
Possible use-cases:
- Control: API calls (CloudTrail) are logged
- Monitor: StopTrail/Change
- Fix: Turn back on
- Control: SSH only from bastion subnet
- Monitor: Create/Change SGs, validate source port if port == 22
- Fix: Change SG via Lambda
- Control: All instances in patch up to date xxx
- Monitor: EC2 Systems Manager + AWS Config rules
- Fix: Patch via Systems Manager
- Control: No root access
- Monitor: CloudWatch Logs + Syslog
- Fix: Isolate and investigate
- Control: No public objects in S3
- Monitor: Object level logging in CloudTrail
- Fix: Make object private
Full Stack
- Establishing platform security
- Establishing network security
- Establishing OS security
- AWS System Manager
- Run command, State manager, Inventory, Maintenance Window, Patch Manager, Automation, Parameter Store, Documents
- AWS System Manager
- Establishing data protection
- Rest: KMS, CloudHMS / Transit: VPN, ACM
Practice
- S.I.R.S
- Security Incident Response Simulations
Visibility
Netflix Usecase
- CloudTrail
- CloudWatch
- SDKs
Security Monkey
- Monitoring resources on AWS
- Respond to different security events on AWS
Awwwdit
- Creates a caching layer in front of API calls
- Caches results of the API describe calls and solves the rate limiting issue